

SIEM
SIEM from Elastic
Detect, investigate, and respond to evolving threats with AI-driven security analytics, the future of SIEM. Apply limitless visibility, generative AI, and advanced analytics. All with the Elastic Search AI Platform, built on open source Elasticsearch.
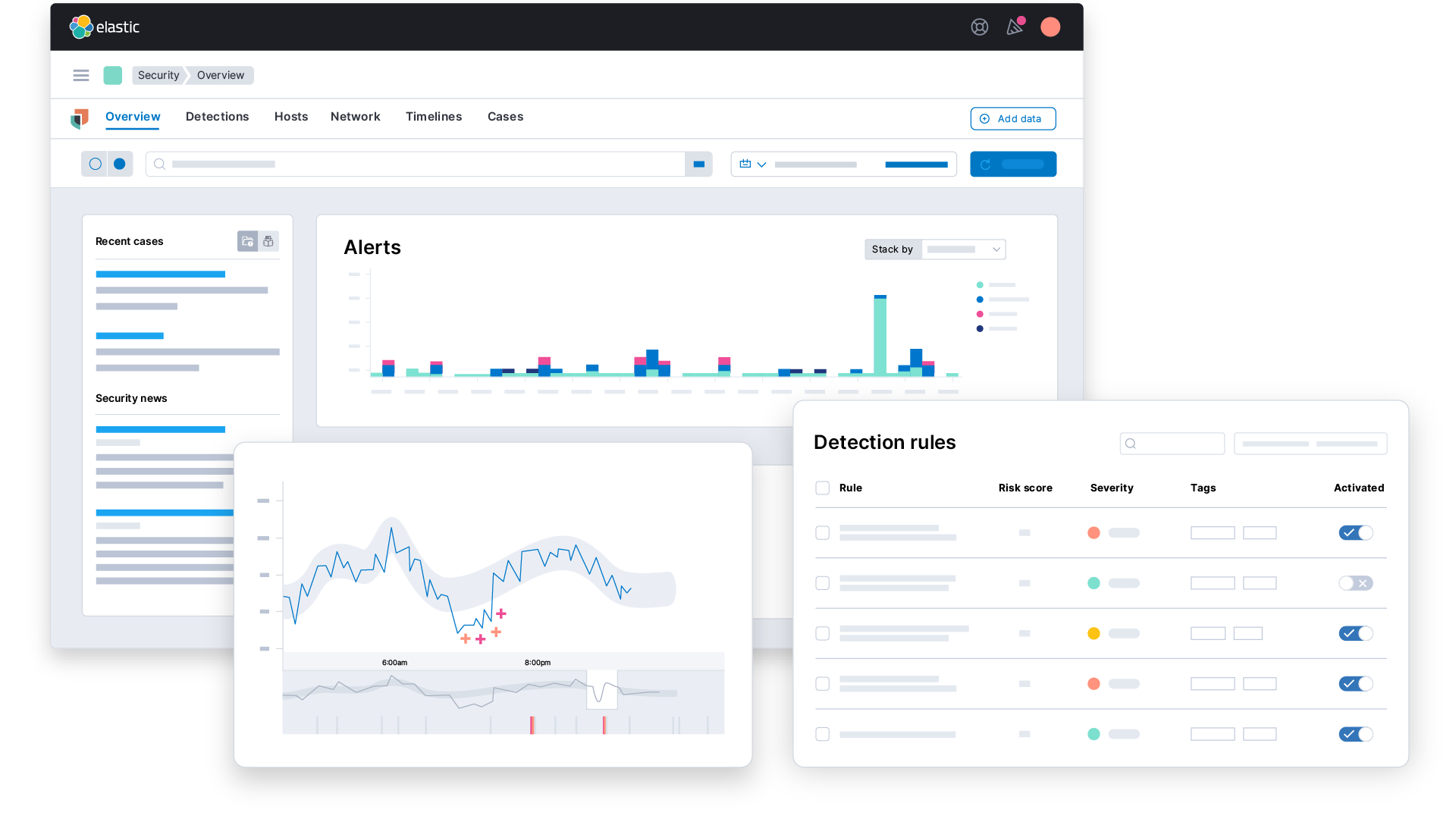
Modernize security operations
Optimize threat detection, investigation, and response with AI-driven security analytics.
Analyze your enterprise at will
Collect and normalize data from across your attack surface — without breaking the bank. Build custom integrations in minutes, not days. Analyze data where it lives. Search archives from the same UI, without rehydration.
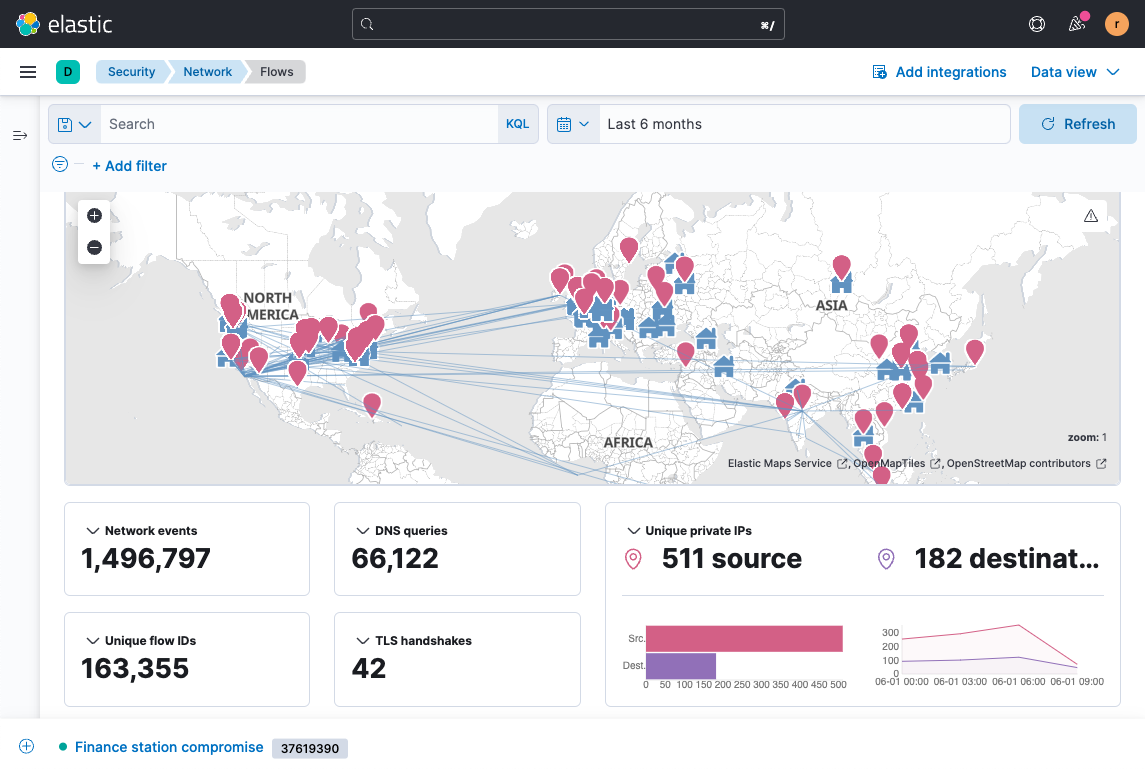
Expedite detection and triage
Automate detection with rules based on research from Elastic Security Labs — all aligned with MITRE ATT&CK® and shared in an open repo. Using generative AI, triage a flood of alerts down to the few attacks that matter.
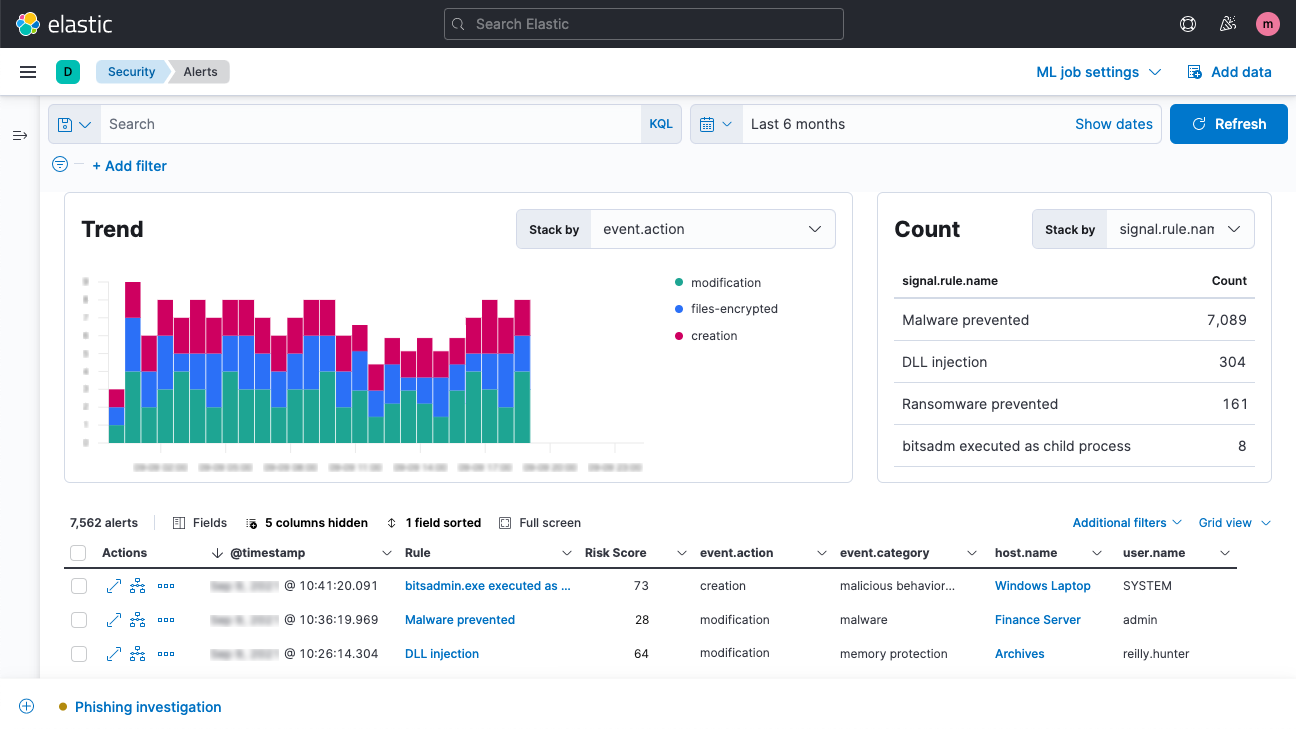
Assess risk with ML and advanced entity analytics
Expose unknown threats with prebuilt ML jobs. Arm hunters with evidence-based hypotheses. Prioritize analysis with behavioral risk scores for users and entities. Uncover threats you expected — and others you didn't.
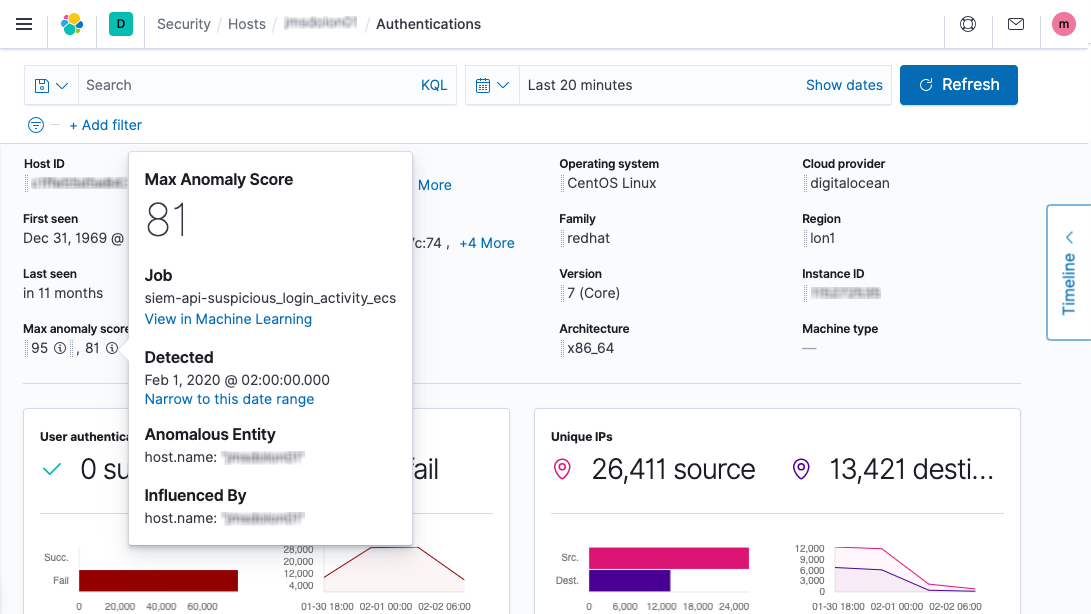
Streamline investigation, automate response
Elevate analysts with AI guidance and expert-written investigation guides. Search iteratively with piped queries. Quickly access contextual insights and data — and gather findings on an interactive timeline. Remotely inspect and respond on hosts. Optimize workflows with external SOAR integrations.
Frequently asked questions
Yes, Elastic Security is a SIEM, and so much more. The solution modernizes SecOps with AI-driven security analytics and offers extended and native protection for endpoint and cloud security. Achieve more with a SIEM solution engineered for tomorrow's threat landscape. See how Elastic Security works in this short SIEM demo.
Elastic Security is one of the fastest growing SIEMs in the industry and has a booming user community. By choosing Elastic as your SIEM, you're equipped with the same capabilities driving many of the world's most mature security teams.
Yes, Elastic Security provides comprehensive threat detection, investigation, and response capabilities:
- Detection: Elastic Security powers threat detection and hunting with advanced analytics, machine learning, and behavior-based rules. It ships with a deep set of prebuilt detection rules that identify malicious activity in real time, reducing the risk of damaging security incidents
. - Investigation: Elastic Security facilitates in-depth investigation by providing fast access to relevant activity data and context. Security teams can explore data from across their attack surface to uncover the root cause and scope of attacks. Features like interactive timeline analysis, generative AI assistance, and case management help analysts understand complex threat patterns
. - Response: Elastic Security reduces MTTR by connecting workflows within and beyond the security operations team, guiding analysts with insights, and facilitating automation. This approach helps security teams mitigate threats quickly, minimize impact, and improve security posture
.
Elastic Security supports the entire lifecycle of security operations, from threat detection and triage, through in-depth investigation, to swift response and remediation.
Yes, Elastic Security offers several ways to connect the other technologies in your environment. With open source Elasticsearch at its core, it provides numerous prebuilt data integrations, plus workflow integrations with third-party ticketing and orchestration technologies, optimizing operations across your enterprise.
Yes, Elastic AI Assistant for Security simplifies the conversion, adoption, and creation of essential SIEM content, including data pipelines, detection rules, queries, and more.
Explore Elastic Security for SIEM
Learn how Elastic delivers a combined impact of 358% ROI and $19 million in benefits.
Analysts need fast access to rich data to fuel hunting, investigation, and beyond.
Explore how Elastic enables the SOC to search vast archives easily and inexpensively.









