Easily ingest data to Elastic via Splunk
As organizations migrate to Elastic from incumbent vendors, quickly onboarding log data from their current solution into Elastic is one of the first orders of business. Data onboarding often involves having to adjust ingestion architecture and implement configuration changes across data sources. We want to ensure that users trialing or migrating to Elastic can get data in quickly to start seeing the power of Elastic solutions as quickly as possible. That’s why we built an integration that automatically maps Splunk-ingested data to Elastic Common Schema (ECS).
In this blog post, we’ll be walking you through this experimental Splunk integration, released in version 7.12 of the Elastic Stack. This integration allows you to keep your Splunk universal forwarders and other Splunk ingest technologies in place, then leverage the Splunk API to get data into Elastic. The integration currently supports the ingestion of Apache, AWS Cloudtrail, NGINX, Windows Event Channels, and Zeek logs, but we have plans to significantly expand the supported data sources.
How does the integration work?
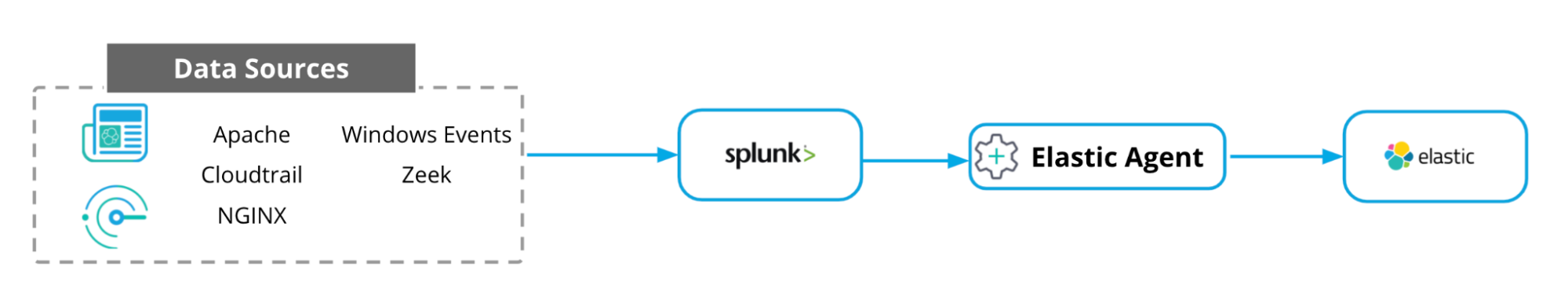
The integration leverages the HTTP JSON input in Elastic Agent to run a Splunk search via the Splunk REST API and then extracts the raw events from the results. The raw events are then processed via the Elastic Agent and existing Elastic integrations.
Configuring the integration
For this blog post, we’ll be configuring the Zeek integration to retrieve existing events from Splunk.
The first step we’ll need to carry out is the installation of Elastic Agent. It’s easy to deploy and supports all common operating systems. You can view the steps to install Elastic Agent and enroll in Fleet here.
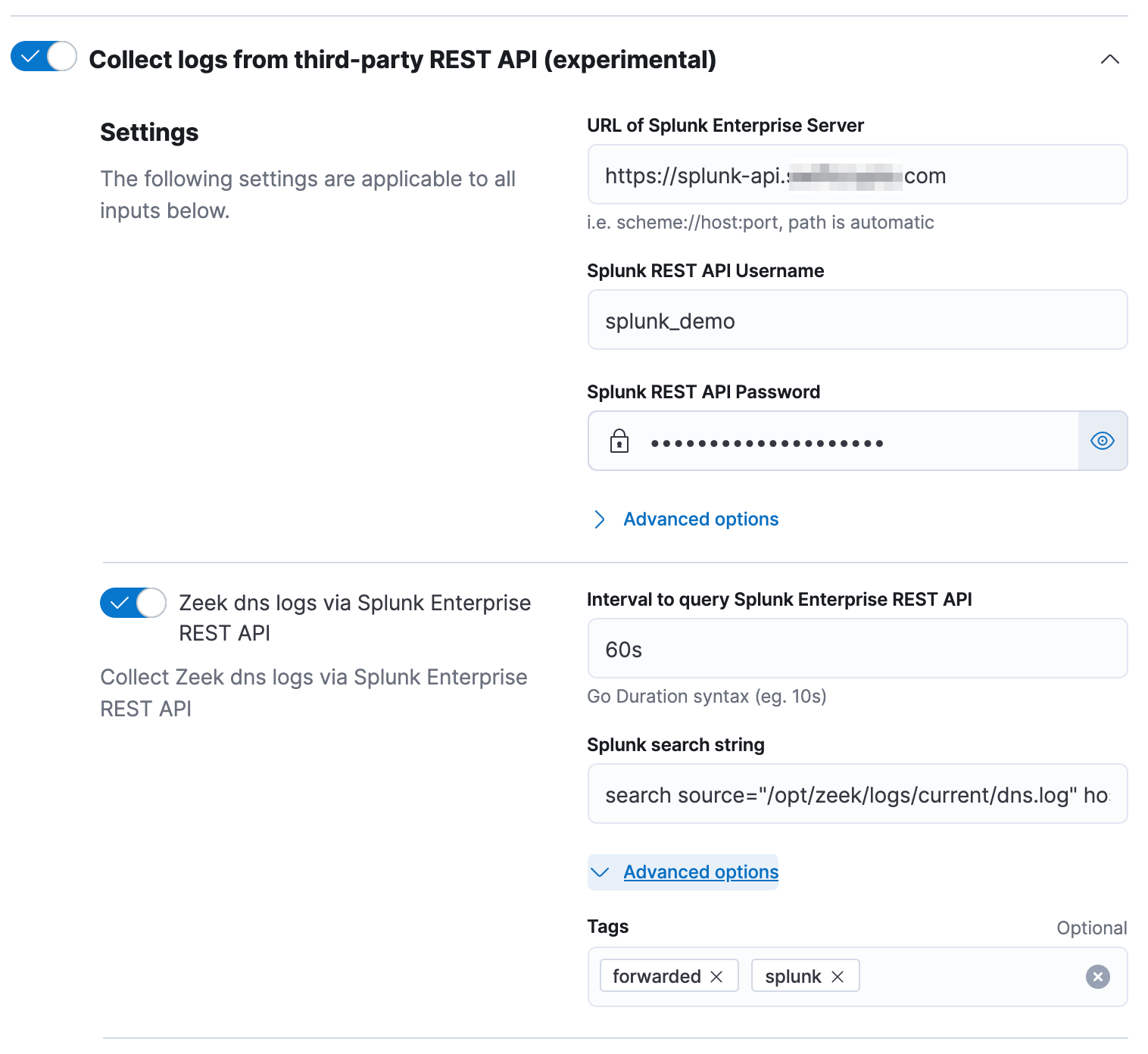
Next, we’ll create a policy and add the Zeek integration. Configure the ‘third-party REST API input’. You’ll need the URL of your Splunk Enterprise Server and credentials to access the API. The Splunk search is customizable, and so is the search interval. Tags can also be added to indicate the logs have been forwarded via Splunk.
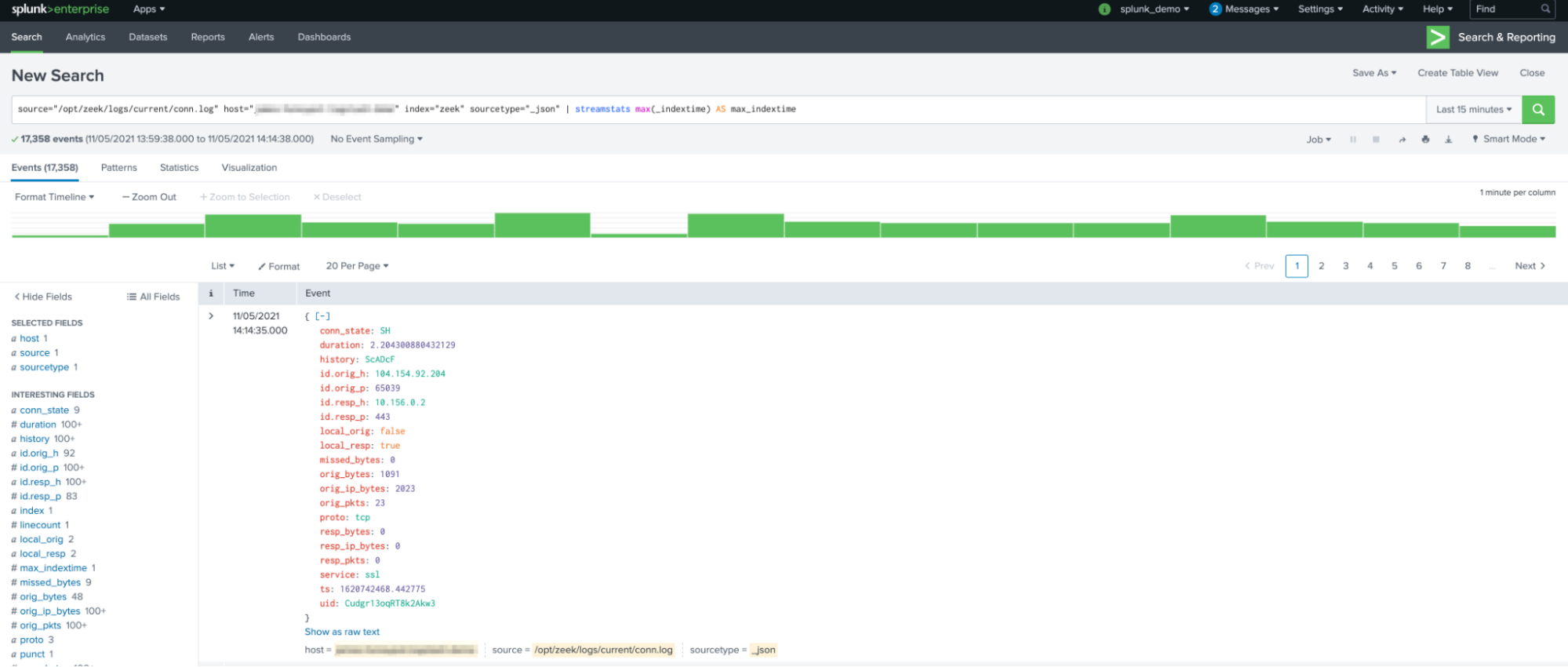
As you can see in the screenshot below, we have Zeek logs streaming into Splunk:
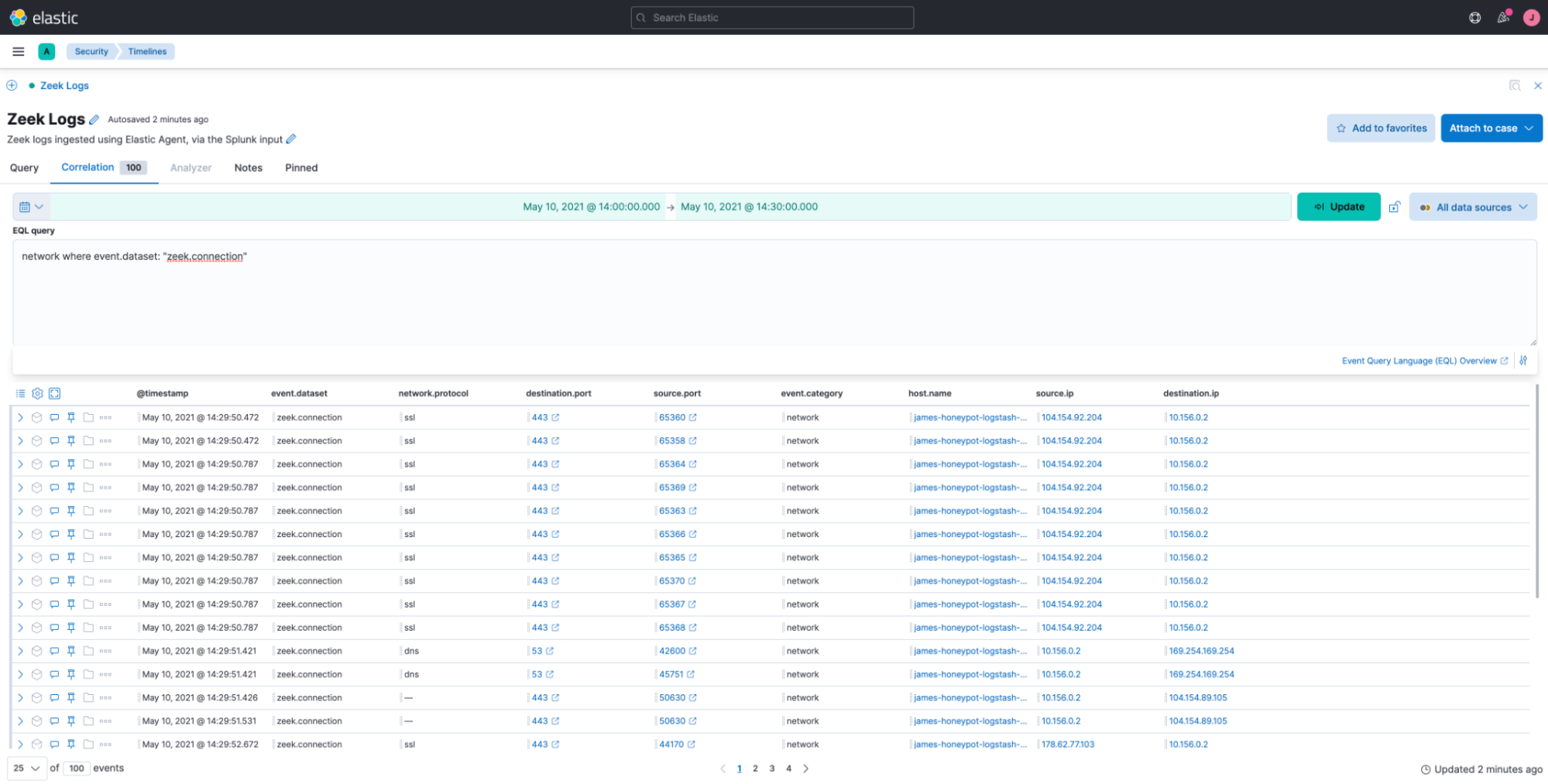
With the Splunk integration enabled, these logs are now available in Elastic:
Splunk + Elastic Common Schema
And now for the best part: all the data ingested via Splunk will be automatically mapped to Elastic Common Schema (ECS). This means you can start leveraging Elastic solutions such as Elastic Security and Elastic Observability right away, without having to worry about manually mapping your data from Splunk’s Common Information Model to ECS.
Analytics content such as machine Learning jobs, detection rules, and visualizations just work! As an example, here’s a Zeek dashboard fully populated with Zeek data ingested via Splunk:
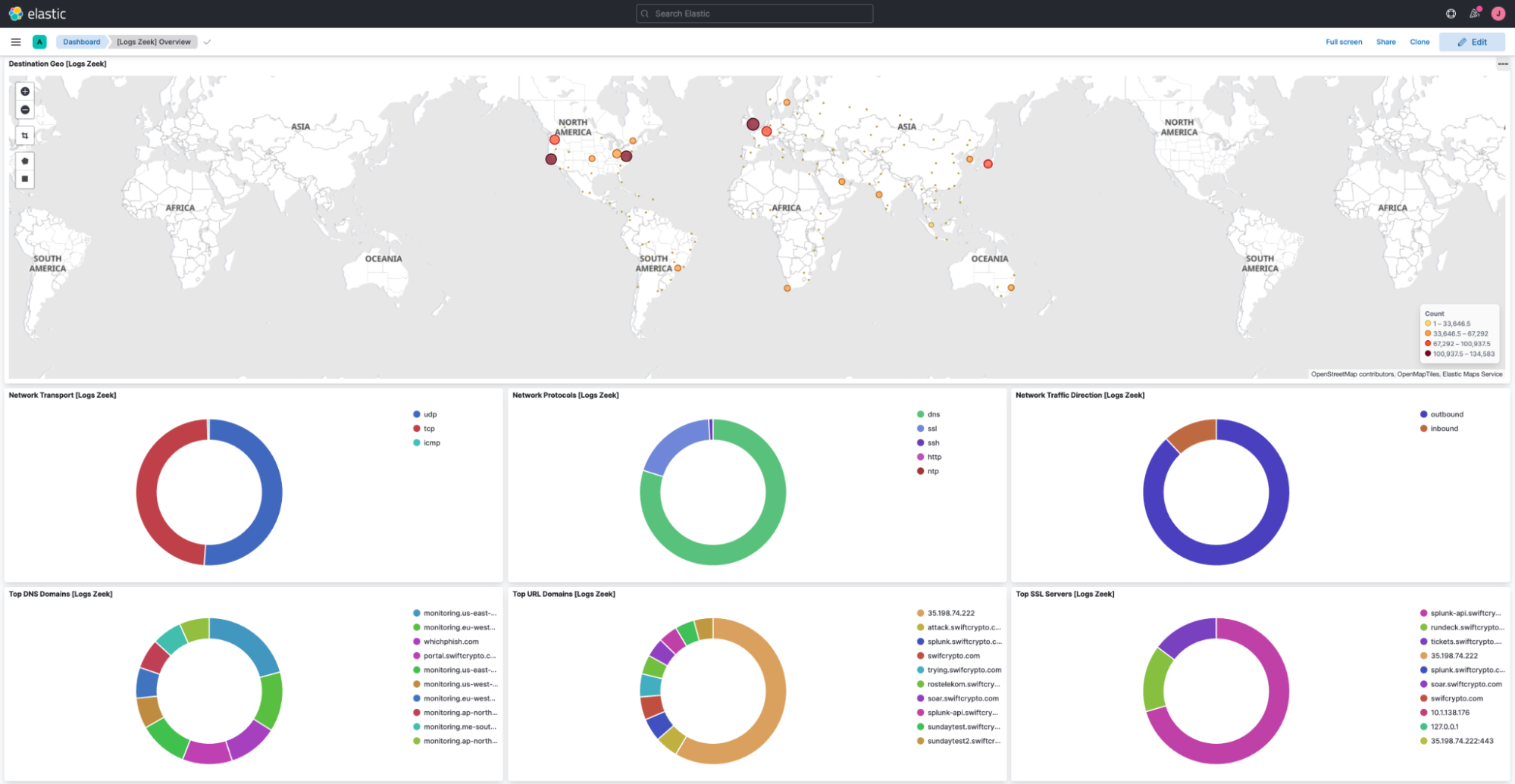
We hope any Splunk user trialing Elastic finds this integration beneficial. Our aim is to ensure you spend less time configuring data ingestion to Elastic and allow you to focus on getting value quickly from our solutions. You can view the associated documentation for the integration here.
We’re very keen to hear your feedback on this Splunk integration. Please let us know what you think on the Elastic Discuss forum or on the Elastic Slack workspace. And if you’ve been waiting for an integration like this before trying out Elastic, this is your moment: Start your free 14-day trial (no credit card required) or download our products, free, for your on-prem deployment. And take advantage of our Quick Start training to set yourself up for success.