Elastic partners with Chainguard on Software Supply Chain security and SLSA assessment

In the aftermath of supply chain breaches against SolarWinds and Codecov, organizations are focused on protecting their software from malicious tampering and compromise. Addressing the complexity of software development and potential security exposures has been top of mind. The complexity goes beyond traditional application security as the software supply chain encompasses and spans across different services, organizations, roles, and responsibilities.
Elastic®, the leading platform for search-powered solutions, is leveraging the Supply chain Levels for Software Artifacts (SLSA, pronounced “salsa”) to resolve this challenge. SLSA is a security framework that consists of standards and controls to prevent tampering, improve integrity, and secure software packages and infrastructure. We enlisted Chainguard to engage in an assessment of our software supply chain using the SLSA framework and to provide a comprehensive and unbiased assessment of potential security threats and strategic initiatives to maintain leadership in securing the software supply chain. Elastic has also deployed forward leading software supply chain security solutions, including software artifact signing using the popular open source project, Sigstore.
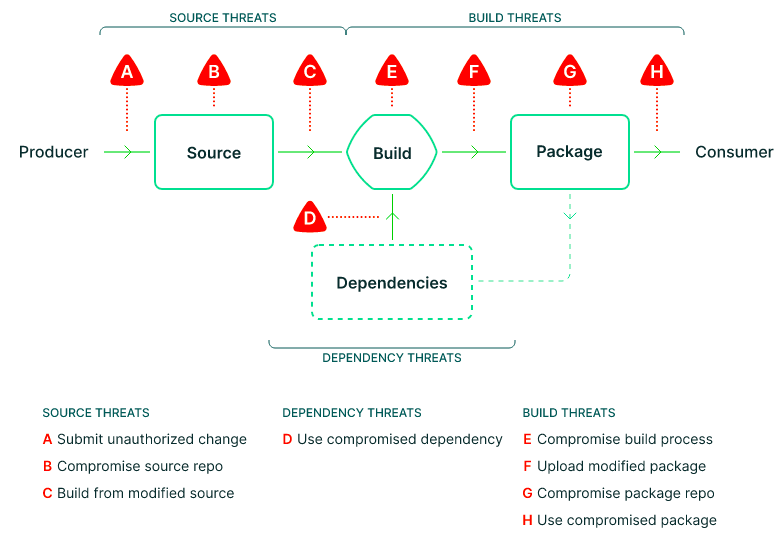
The Elastic SLSA assessment was the largest SLSA assessment carried out by Chainguard to date. To understand the scale of the risks, everything that sits between the producer and consumer of software is a potential attack target in the supply chain.
To unfurl the complexity and build a threat model, we begin by breaking the software supply chain into its critical components
- Source
- Build
- Dependencies
- Package
Knowing what your software supply chain consists of and what threats are posed is a good starting point — but how do you go about securing it?
Why SLSA?
SLSA has grown to become one of the most approachable frameworks for enterprises and open source software projects looking to adopt software supply chain security practices to defend against common supply chain threats. With its software supply chain security capability model, which can be adopted incrementally, SLSA helps answer questions like “How do I trust the code I’m using hasn’t been tampered with?” and “How do I trust the build system or source code system used in producing this package?”
Scope and goals
When adopting SLSA, Elastic sought to take a threat-based approach to create an overview mapping and threat assessment of its software supply chains. There were three clear goals to accomplish in the company’s existing software supply chain security architecture, which map to many of the practices and principles outlined in the SLSA framework:
Isolate to reduce impact and escalation
Strong access controls to maintain integrity
Verify software integrity at each stage of the supply chain
The assessment
The Elastic SLSA assessment was the largest SLSA assessment to date. For the assessment, Chainguard used a three-phase approach:
- Phase one: The Chainguard team focused on understanding Elastic's current state of supply chain security practices by interviewing key essential stakeholders.
- Phase two: The Elastic team gathered information about every software supply chain that produces an artifact that gets distributed and made available to their customers, along with Elastic points of contact responsible for those supply chains. The Chainguard team interviewed these points of contact about all aspects of the supply chain, assessing them against SLSA.
- Phase three: Chainguard closed the assessment with a survey of the Elastic team to compare results from the previous phases and the completion of the assessment.
Elastic takes advantage of a number of technologies across multiple teams to deliver code, and meeting these teams individually was an important aspect in gaining full insight into the various software supply chains. Several of the Elastic solution components are free and open, and with that, Elastic accepts contributions from open-source developers, customers, or others from the Elastic community. All this was taken into consideration across the SLSA assessment to capture existing SLSA security practices per project and recommendations for Elastic’s overall software supply chain security roadmap.
The assessment followed SLSA v0.1, which emphasizes a set of software supply chain security practices that deal with source code, the build process, and provenance with an emphasis on machine-readability and machine-verifiability. The Open Source Security Foundation (OpenSSF) released SLSA v1.0 in April 2023, after the completion of the assessment.
Strategic initiatives
As outcomes of the SLSA assessment, Elastic has implemented strategic actions to ensure the security of the Elastic software supply chain.
SLSA helps pinpoint specific risks and threats a malicious actor may attempt to disrupt development, build, and delivery systems. As a response, Elastic added over 40 new detection rules to its deployment of Elastic Security and continues to work with technology partners in source control and CI/CD orchestration on enhancing detections in these areas.
To encourage increased focus on supply chain risks among security researchers, Elastic has increased the awards for supply chain threats reported via the Elastic Security Bug Bounty.
To provide an easy way for users to verify the provenance of Elastic container images before deploying them to any infrastructure, Elastic is now releasing all Elastic Stack container images signed with Sigstore.
Conclusion
The SLSA framework is a valuable tool for assessing risks and defining specific mitigation actions. Elastic looks forward to sharing future updates on our approach and solutions for solving supply chain security challenges.
Organizations interested in a software supply chain security assessment can contact Chainguard. And anyone interested in educational materials on SLSA can find them on Chainguard Academy.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.

